Making Solana privacy-friendly — The Elusiv Deep Dive
A peek into the world of ZKPs, how Elusiv is solving privacy on Solana while being compliant, and the range of possible applications on Elusiv!
The arrest of Tornado Cash developer Alexey Pertsev last year shocked the whole crypto community, making privacy one of the most difficult and scary areas to build in! However, it’s well-known that privacy is a necessary primitive for DeFi and web3 payments to work at scale.
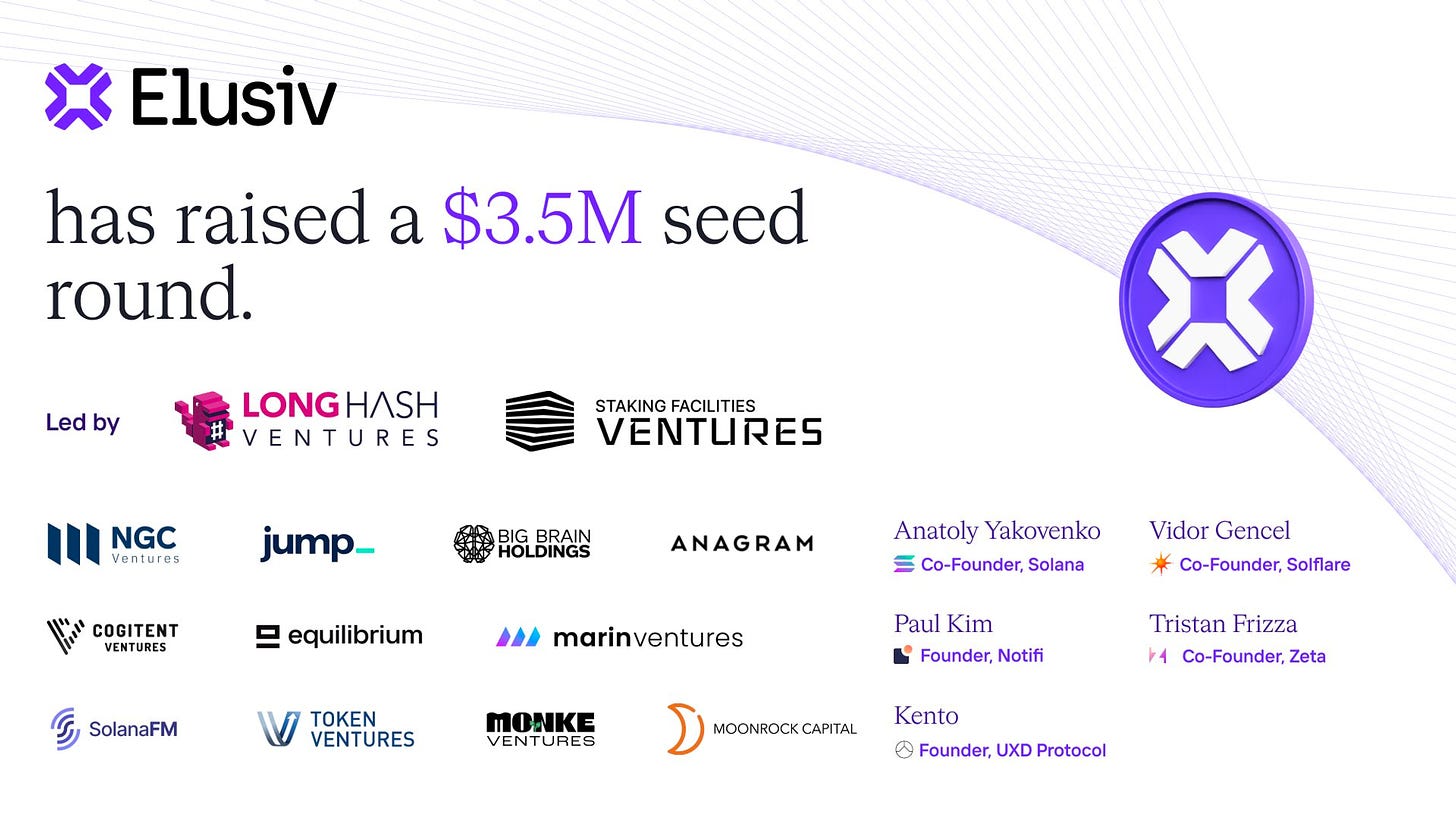
Leading this privacy revolution is today’s spotlight project — “Elusiv,” which started as just a Solana Hackathon Project to raise a $3.5 Million seed round to become the #1 privacy protocol on Solana Mainnet!
Problems: Why do we need Elusiv?
Any public blockchain is, by default, transparent: anyone can view the entire history of transactions.
For instance, if you are paying a merchant using Solana, they can check your balance and transaction history via your wallet address. If anyone is receiving their salaries on-chain and you know the wallet address of that person, you can get to know their salary, which is supposed to be private information!
To enable true crypto adoption, most businesses must be on-chain, accept crypto, pay their suppliers in crypto, and manage treasuries on-chain. But what’s stopping them? Imagine a very cool e-commerce D2C company that sells protein bars and is completely on-chain. They accept payments and pay their raw material vendors, and employees in crypto have NFT-based invoices. But since it’s on-chain, any of their direct competitors can simply get to know their valuable granular data like margins, sales, and origin of raw materials, which can destroy that company’s competitive advantage! Unless a business isn’t very unique and has nothing much to defend, they wouldn’t like to go on-chain for privacy reasons. Likewise, any customer can see the revenue and balance of the merchant store. Transparency is not always king :)
The key problem we need to think about is how we achieve privacy in Web3 without sacrificing security, safety, and decentralization.
What exactly is Elusiv?
Elusiv is a privacy protocol built on the Solana blockchain that enables users to access universal encryption. It uses advanced zero-knowledge cryptography (zk-SNARKS) and multi-party computation to ensure that user data remains fully private while the network can still uphold integrity, security, and compliance. This way users get tools to control their data empowering them to choose what gets shared and what doesn't.
How does it work?
More the number of users and diversity of transactions, the better privacy. This is the simple fundamental backbone of how Elusive works. Now let's dive deeper to understand what actually goes under the hood while it solves the need for privacy in blockchains.
As there are more users and a variety of transactions, it makes it more challenging to link deposits and payments over time. Users can keep their balances private by letting their funds get put together in the pool with others while keeping track of associated secret values. The Warden Network forwards requests from the user side to the blockchain, preventing funds' deposits and payments from being linked to the user's public key (which we don’t want to show here).
In the upcoming section, we will delve into the technicalities of Elusiv and cryptography, providing a more detailed understanding of the technology. This information will complement the general overview provided in the earlier section.
How do you keep it a secret?
Imagine you have a secret message or value that you want to keep safe, but you're not ready to reveal it just yet. To protect it, you use a special tool called a hash function. This tool takes your secret message and turns it into a special code called a hash.
Cryptographic hash functions are a type of function that takes in digital data and produces a unique, scrambled output called a hash. Now, you send this hash code to someone else, who you trust to keep it safe. Later, when you're ready to reveal your secret message, you give them both the original message and the random value that you used to make the hash code.
The person you gave the hash code to can then use the same tool (hash function) to turn the original message and random value into a new hash code. If this new hash code matches the one they received from you earlier, then they know that your secret message hasn't been changed or tampered with. This technique is called a hash-based commitment scheme and is commonly used for secure data storage.
The role of commitments in Elusiv is to ensure that users can deposit funds into the system and later claim those funds while maintaining the privacy and security of their transactions.
When a user deposits funds of a certain asset type into Elusiv's shared pool, a commitment is created and stored on the blockchain. This commitment is derived by hashing together the amount of funds deposited, the asset type, and a secret value known as a nullifier.
Later on, when the user wants to claim the funds they deposited, they must provide proof that they know the nullifier associated with the commitment. This proof must be created in a way that does not reveal the nullifier itself, ensuring that only the user who deposited the funds can access them.
This hash function has three main security properties that make it useful for cryptography:
Preimage resistance: It is impossible to retrieve the original input data from its hash value. This means that given a hash, it is impossible to determine the exact digital data that was used to produce it.
Second preimage resistance: It is impossible to find a different input that produces the same hash value. This means that given input data, it is impossible to find another input that produces the same hash value.
Collision-free: It is impossible to find two different inputs that produce the same hash value. This means that no two different digital data produce the same hash value.
Hash functions are an essential tool for creating cryptographic primitives and protocols, as they can be used to provide security and privacy guarantees. For example, in Elusiv, a commitment scheme may use a hash function to commit to a specific value without revealing it. In contrast, zero-knowledge proofs may use a hash function to verify that a statement is true without revealing the actual information.
zk-SNARKS and Elusiv
ZKPs (Zero Knowledge Proofs) are used in the form of zk-SNARKs (zero-knowledge Succinct Non-interactive Arguments of Knowledge with the Groth16 algorithm) are a way to prove that a computation was done correctly without revealing what the inputs were. They are fast and easy to check (as they can be derived without the need for interaction between the prover and verifier).
In Elusiv, ZKPs are used to prove that someone knows a code called a nullifier, without revealing the actual code. This is important for privacy and security because if the nullifier was revealed, someone could track the person's spending or intercept their commitment. By proving they know the nullifier without showing it, the person can claim their commitment without worry.
The nullifier is also stored on the blockchain to prevent double-spending on the same commitment. This ensures that each commitment can only be claimed once, maintaining the integrity of the system.
But how do they manage compliance?
The main legal risks of building a privacy solution like Elusiv involve the fact that the mixing functionality they provide can be used to facilitate money laundering and other criminal activity.
Elusiv is able to achieve this with the help of “Viewing keys”. These keys allow users to generate and share access to specific transaction details. Each Elusiv account has a spending key and a root viewing key. The spending key is used for spending assets (should NOT be shared with anyone, as it is similar to sharing your private key), while the root viewing key is used for decrypting assets. By sharing the root viewing key, a trusted individual can be granted full view access to private assets without the power to spend them.
Further, certain AML practices can be applied like:
Transaction caps: For instance, a transaction cap of $10,000 can prevent hackers from moving large funds quickly via Elusiv.
Relayer-based address checks for direct connections to illicit/hacked funds.
Decentralizing the viewing authority — The ability to generate the viewing key can be threshold sharded amongst all the validators, who would then be able to decrypt transactions in response to a governance vote. It would then be up to governance to vote to decrypt transactions that are in the interest of the network, such as the movement of hacked funds or to comply with a valid request from law enforcement agencies.
Balancing privacy with regulatory requirements is the key forward. To do this, organizations can grant different permission levels to users while ensuring compliance with local financial rules and tax regulations. This approach enables Elusiv to maintain its privacy-focused platform while complying with regulatory requirements.
Ideal User Experience:
Wallets are the most critical part of the Web3 UX, as all the interactions between a user and the blockchain happen via them. To enable true adoption and the most seamless UX for users to make private payments, direct Elusiv integration with wallets would be killer!
Imagine you are using Phantom wallet, and while sending USDC to your friend, you have to option to select private payments via Elusiv. The user shouldn’t have to worry about shielding and unshielded or, in fact, interacting with Elusiv. Everything automatically happens in the backend.
This can be similarly integrated as embeddable widgets in other wallets like Backpack, Glow, Solfare, and so on! Further, paying in any token would be critical, as someone who simply wants to send USDC to anyone privately should have the flexibility to pay the gas fees in USDC. Elusiv team is already working on this!
Traction and Community:
Elusiv has raised a $3.5 million seed round from marquee investors like LongHash Ventures, Staking facilities ventures, Jump, Big Brain, and angel investors like founders of Solana, Zeta, Solfare, UXD, and Notifi — giving it enough firepower for the next 1-2 years. It has already crossed $300K+ in organic volume for zk-encrypted transactions. Further, it’s audited by Ottesec and ABDK.
On the community front, Elusiv has been actively building community via initiatives like Breakpoint, Superteam Ecosystem Call presentation, sponsoring sandstorm and encode hackathon, and so on.
The teams had already started building during their private testing. With Typescript SDKs coming up, we believe the traction will shoot up, as developers can easily integrate with just 4 lines of code!
What can be built using Elusiv?
Solana Pay x Elusiv: Solana Pay is a payment standard that enables merchants and e-commerce platforms to accept payments via crypto — using Solana, it enables payments at new zero cost and instant settlements. However, privacy remains a major concern, and all traditional counterparts like Apple Pay and Paypal offer privacy to their users, which hinders its mass adoption.
By integrating Elusiv and Solana Pay, one can build a private payments solution in the following ways:
Direct Integration with Solana Pay Framework: This will enable anyone building with the Solana Pay framework to choose the privacy option, starting with Solana Pay transfer transactions.
Checkouts: Enable users to choose private payments at Solana Pay checkouts without directly integrating with the Solana Pay framework. 2.
DeFi: Undoubtedly, DeFi is the biggest use-case for Privacy, as it’s critical to build the next generation of Finance. A few areas in which, DeFi can leverage privacy are:
Private Swapping and Staking
Trading on-chain via DEXs, while not revealing your PnL and strategies to others.
Depositing in a Money Market and LP’ing
On-chain Dark Pools
Private Token vesting
Specific Private wallet, built for DeFi interactions
CBDCs: CBDCs are intended to be anonymous like Cash, where you can’t really trace where the piece of paper came from! To allow for the privacy of transactions like cash, Elusiv can be leveraged to enable privacy-protected payments and transfers on-chain. Further, Central Banks can have control over the viewing authority for illicit transactions, making it a better alternative than even cash!
Privacy-enabled zk rollup on Solana: This will be similar to Nightfall by Polygon and EY, where the transactions on the chain will be private by default while leveraging all features and composability with the Solana Mainnet.
Privacy-enabled NFT Mints: To enable NFT traders to mint and trade NFTs privately, Elusiv can use them to fund private balances and then mint the NFTs without revealing the mint amount.
Zk-based communication: Encrypted wallet-to-wallet communication. Think Protonmail but entirely on Solana with no off-chain storage — Only Possible on Solana due to cheaper fees!
Institutional-friendly use cases: Privacy can be a great application for wholesale or institutional use cases where the parties would prefer private transactions. Digital signatures powered by ZKPs are secure, private, and verifiable, without revealing sensitive information about the signer or the transaction itself.
Encrypted NFTs for businesses: In business use-cases like Invoicing, Encrypted NFTs can be used, where the face of the NFT is on-chain and public, but the metadata is encrypted via ZKPs, making it suitable for tokenizing invoices, purchase orders, etc., which contains sensitive pieces of information such as profit margins.
Lending and Borrowing: To enable programmatic credit scoring while preserving privacy, borrower repayment history can be anonymized but cryptographically proven accurate. This approach also fosters on-chain transparency. Using Elusiv can provide enhanced privacy, which is particularly important for larger institutional borrowers who want to safeguard their inventory of assets and cost basis. Underwriters (on-chain or off) can verify relevant data while protecting market-makers from disclosing their book. This bridges the non-technical gap and facilitates trust in the credit scoring process.
Privacy-based Stablecoin: To add a layer of privacy to stablecoins, a privacy-focused stablecoin leveraging Solana's scalability and speed could provide secure and easy-to-use Zero Knowledge transfers. The stablecoin should prioritize security, reliability, and user-friendliness. Potential use cases could include
Anonymous public donation platform to protect donor privacy.
Fundraising and grant platform that ensures public privacy.
Peer-to-peer payment splitting.
Private business payments to protect transaction details from the public.
Secure online marketplaces enabling private transactions between buyers and sellers.
Privacy Landscape on Solana:
The ZKP landscape on Solana is still nascent but rapidly developing:
Light Protocol: One of the direct competitors to Elusiv will be Light Protocol, which has raised $4.2 Million from investors like Polychain Capital, and Solana ventures. Light protocol v1 has shielded more than $1.5 million in transactions with 2k+ users, showing some significant transactions. It also has a user-facing app for private transactions as well as SDKs for developers.
SPL Token 2022: SPL is the token program on Solana, defining the implementation of fungible and non-fungible tokens. The Token 2022 upgrade allows for confidential transfer standards, allowing organizations to embed confidential transfers and balances with few lines of code. This is not a direct competitor to Elusiv but another addition to the Solana privacy ecosystem. The Confidential Transfer extension to Token 2022 will make it possible to do confidential payments (but not anonymous — which Elusiv solves).
Other solutions, like burning wallets/stealth addresses or using an omnibus wallet hot wallet of a trusted intermediary, can also be used for privacy. Besides, Project Cyclone by Jump Crypto also focuses on ZK innovations. There was another project called Otter Cash, which was working on privacy protocol, but has now pivoted to Renegade.
Privacy solutions on other chains:
The privacy landscape on other chains can be divided into:
Transaction Level:
Solutions with their chain: Zcash and Monero are prominent solutions, with Zcash being more compliant using ZK-SNARKS, while Monero promises absolute anonymity. For all these projects, the sender and receiver must be on the same blockchain to transact, limiting interoperability and requiring transacting on their native volatile tokens.
Rollups: Polygon Nightfall is a good example of a privacy-enabled rollup, suitable for institutional use cases.
Smart Contract Level: Tornado Cash, Calamari Network, Silent Protocol, and Railgun — smart contract level mixing service generally uses zk-SNARKs.
General Purpose:
Own chain: Secret Network and Oasis Network
Rollups: Azetc (the leading privacy-based rollup on Ethereum)
ZK on Solana: More than Privacy
Zero-knowledge (ZK) has two primary components: interactive proof and privacy. While verifiability is beneficial, it can be achieved without privacy. Verifiable compression allows for efficient million-step computations to be performed off-chain, followed by a quick on-chain verification check, resulting in accurate and condensed computations.
Privacy adds to the complexity of ZK and makes it even more intriguing. While blockchain transparency is a selling point, businesses require a certain level of confidentiality, which can be achieved with ZK. It allows the validation of a statement's truthfulness without disclosing the statement itself, potentially leading to the development of applications as secure as the blockchain itself while preserving data confidentiality.
ZK can be understood in terms of two concepts: computational asymmetry (verifiable computation) and information asymmetry (Zero-Knowledge proofs). Verifiability is the primary characteristic, and privacy is an optional feature that can be used depending on the circumstances. Furthermore, ZK extends beyond privacy and has multiple scalability features that are transforming the range of blockchain applications.
It will be interesting to see ZK technology being leveraged for “interactive proofs” on Solana rather than just privacy — for instance, sovereign zk-rollups on Solana.
Closing Thoughts:
ZKPs have already been demonstrated in real-world scenarios through projects such as Zcash and Monero. These projects have significantly advanced ZKP research and implementation, but practicality and usability have been challenging. It is also important to prioritize safety while achieving privacy. In order for Web3 to become widely adopted, it is essential to have complete privacy. Elusiv is among the new generation of projects that aim to make ZKPs more practical by developing a range of tools that address both sides of the privacy spectrum while building on one of the most performant blockchains and vibrant ecosystems — Solana! 🚀
Cheers for staying with us — are you excited about what’s next in the privacy frontier of Solana?!
Share it with friends if you found it helpful! For any project inquiries or suggestions, connect with — Sitesh Sahoo and Yash Agarwal.